Why 45 % of support tickets are avoidable
Tickets pile up. Costs rise. Momentum fades. Now imagine the opposite: fewer tickets, faster resolutions, smoother operations.
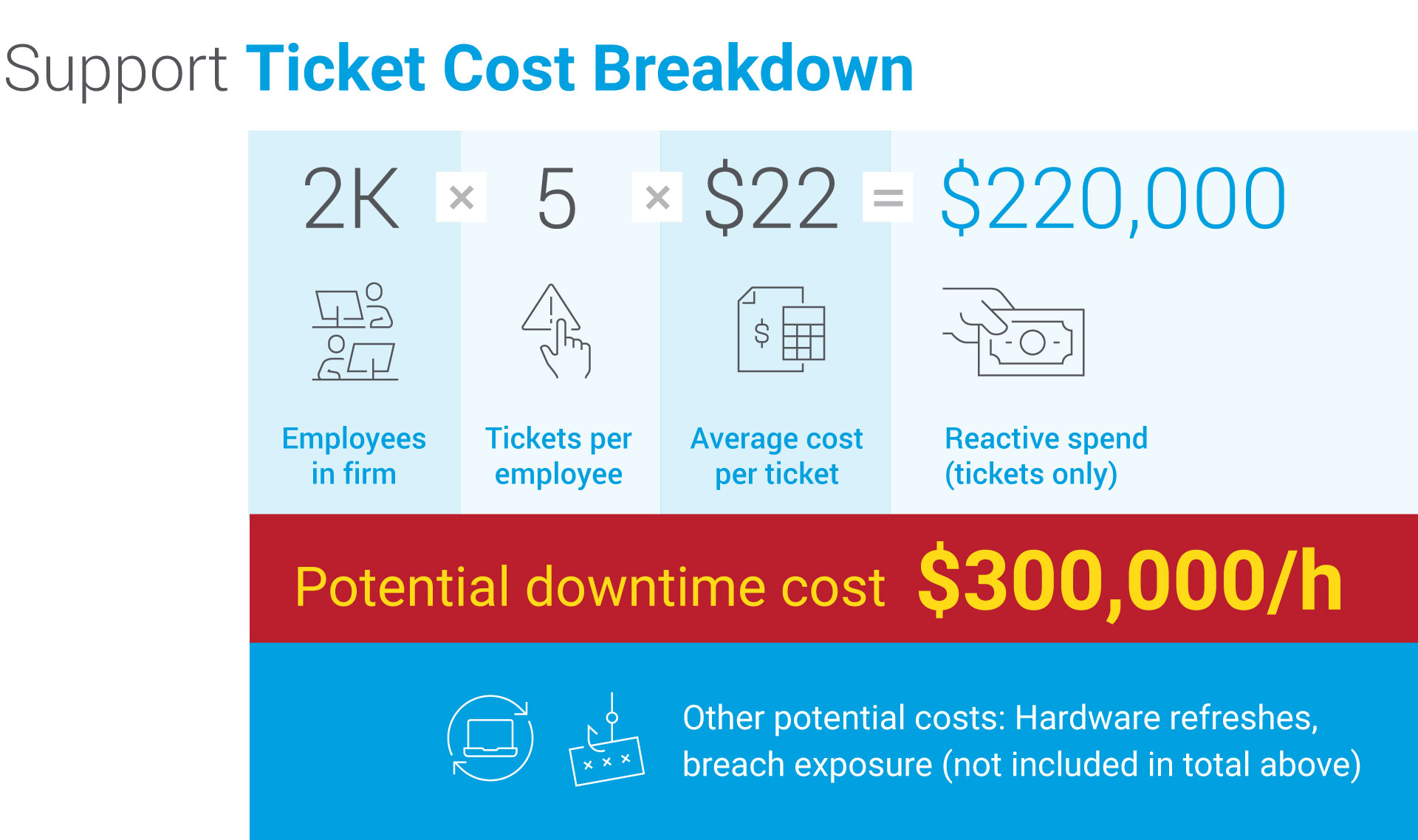
With 2,000 employees generating an average of five support tickets each, at a cost of $22 per ticket, the company must manage 10,000 tickets and $220,000 in reactive support expenses, even before adding hardware renewal costs, exposure to cyberattacks, or potential downtime that can exceed $300,000 in losses per hour. The numbers are staggering, but the opportunity is immense. With a modern strategyend-user computing (EUC), you reduce the volume of tickets, speed up the mean time to resolution (MTTR) and achieve a return on investment in less than 12 months. Here are five game-changing levers.
The real cost behind “just a ticket”
A ticket is never “just a ticket.” It’s time and escalations. It’s a distracted employee and delayed delivery. It’s the cumulative weight of outages and the shockwave of identity attacks that often begin at the service desk.
The real one cost of service in EUC is based on four pillars: support and tickets, capital expenditure / hardware renewal, downtime, and cyber risk. Ignoring any one of these throws the whole off balance—especially as modern ransomware groups leverage social engineering on help desks to reset multi-factor authentication (MFA).
Lever 1: Hybrid virtualization (Citrix / AWS WorkSpaces)
Centralize the workspace. Reduce local outages. Simplify management. Expect calmer queues thanks to fewer endpoint incidents and rapid, template-based deployments. Thin clients combined with shared images also limit drift and delays.
To be implemented
- Non-persistent groups for task/knowledge role employees
- Image lifecycle with ring releases
- Auto-scaling policies with budgetary safeguards
Signals to watch for: Session latency, connection duration, profile loading time, image health.
Lever 2: Self-service & automation
Reset passwords without waiting. Deploy patches remotely, on time. Script the solution before the complaint even arrives. A large portion of service desk volume comes from resets; moving this to self-service eliminates wait time. And the risk of social engineering.
5 Profitable Automations
- Password Reset/Unlock
- Software installation/assignment
- Disk Cleanup and Storage Recovery
- Repair/renewal of Wi-Fi/VPN profiles and certificates
- Printer Mapping
Lever 3: Predictive supervision
Listen to your fleet. Device and session telemetry (latency, storage health), policy drift, and crash loops whisper faint signals before users feel the pain. Triggers fire, remediation executes, and the incident ends behind the scenes.
Guide
- Collect : endpoint metrics + sessions, change events
- Detect : drift and early warning thresholds
- Act : self-remediation; only open a ticket if automation fails
Align these practices with the “Visibility & Analytics” pillars of the Zero Trust frameworks (see CISA — #StopRansomware Guide).
Lever 4: Extend material cycles
Move the load off the terminals. VDI / DaaS Transfers computing power to the data center or cloud. Thin, stable clients last longer, consume less power, and require less on-site maintenance. Renewal becomes a rhythm, not a disruption.
To change
- Standardize thin/zero clients for virtualized roles
- Separate device renewal from the compute lifecycle
- Follow the total cost of ownership (TCO) devices (CAPEX, energy, support)
Lever 5: Employee experience & single sign-on
Give users a single entry point. Make it secure and obvious. A modern gate with SSO reduces login friction and channels common requests into guided self-resolution. Use a Phishing-resistant MFA (FIDO / WebAuthn) to cut off a common intrusion route: help desk spoofing (see NIST SP 800-63B).
- Application catalog with optimized paths (minimum clicks)
- WebAuthn / FIDO Enrollment Flow
- “Resolution tiles” for common queries
Mini case: Air Canada
Challenge : Frequent incidents, traditional VDI under pressure, overloaded support.
Approach : Modernize the EUC platform, streamline management, implement proactive monitoring, migrate in phases.
Results in 9 months:
- Total incidents: −45 %
- Major incidents: −67 %
- Normal incidents: −83 %
- KING positive from the 7the months. Stabilized environment, increased productivity, reduced support pressure.
Conclusion
The combination of “hybrid virtualization + automated self-service + predictive monitoring + phishing-resistant SSO/MFA” simultaneously reduces tickets, MTTR, TCO, and risk. Measure, iterate, and reinvest.
FAQ
What should be automated first to reduce tickets?
Start with password resets/unlocks, software installation requests, multi-factor authentication re-registrations, Wi-Fi/VPN profile fixes, printer mapping, and disk cleanup/driver repairs. Link each action to “To Fix” self-service tiles. Most organizations see an immediate decrease in MTTR and a more stable ticket queue.
Should everyone move to VDI/DaaS?
No. Use personas. Virtualize task workers and most knowledge workers; keep experts or hardware-dependent roles on physical workstations or GPU-enabled groups. Migrate in rings to limit risk.
How to prove ROI in less than 12 months?
Establish a baseline with ticket count and cost per ticket (22 $ in your model). Track self-service %, MTTR/first contact resolution (FCR), incident count, and device TCO. Compare variances to EUC program expenses, including incidents avoided and longer renewal cycles.
Can we extend hardware renewal without harming the UX?
Yes: Move compute to the data center and keep thin clients longer. Monitor connection time, session latency, and application launch as safeguards. Replace devices as needed and maintain thin images.
How does SSO/MFA reduce both tickets and risks?
A single portal reduces login thrash; phishing-resistant MFA (FIDO/WebAuthn) prevents spoofed resets at the help desk. Add a strict re-verification when changing MFA devices and automate the flow.
What signals should you watch for for proactive corrections?
Session latency, profile load times, disk health, policy drift, and app/driver crash loops. Alert, automatically remediate, and only open a ticket if automation fails.
Quotes & Links
NIST SP 800-40r4 – Enterprise Patch Management Guide (2024) — why disciplined application of patches reduces risks.
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-40r4.pdf
NIST SP 800-63B – Digital Identity Guidelines (Phishing-Resistant MFA).
https://csrc.nist.gov/pubs/sp/800/63/b/upd2/final
CISA – #StopRansomware Guide (2025) — Help desk impersonation remains an active vector; use phishing-resistant MFA.
https://www.cisa.gov/sites/default/files/2025-03/StopRansomware-Guide%20508.pdf
DOE/OSTI – Zero-Client Computing: Lifecycle Savings — thin/zero clients show notable TCO gains.
https://www.osti.gov/servlets/purl/1477585
MDPI (peer reviewed, 2025) – Predictive maintenance reduces unplanned downtime.
https://www.mdpi.com/2071-1050/17/9/3926
MetricNet – Definition and Scope of Cost Per Ticket.
https://www.metricnet.com/service-desk-cost-per-ticket-motm/
Noticed : Where this article cites 22 $ per ticket, industry standards are often between 15 $ and 25 $; confirm your actual cost per ticket from the ledger and volume before modeling.




